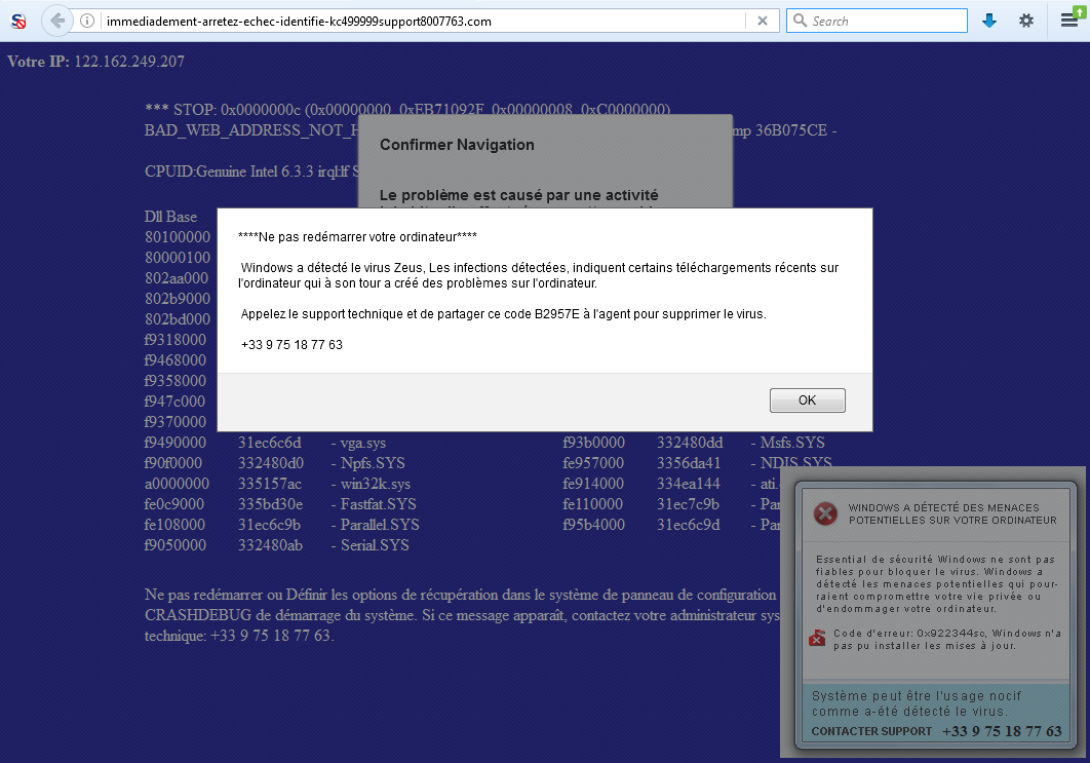
A few days ago, I received a panicked call from my parents who had somehow managed to land on a (now defunct) web page (snapshot here) claiming they had been infected by Zeus. This horrible HTML aggregate had it all: audio message with autoplay, endless JavaScript alerts, a blue background with cryptic file names throwing us back to Windows' BSoD days, and yet somehow it displayed a random IP address instead of the visitor's one.
First call:
After everyone had a good laugh on Twitter, I decided I would give them a call to know more about what they hoped to accomplish. So I fire up an old Windows XP VM, and get in touch with the "tech support". I am greeted with a pre-recorded message, then Patricia is kind enough to anwser my call. I immediately try to get her hopes up by telling her that I'm a businessman working on an important, high-figure contract, and that time is of the essence. Sadly, it turns out that her French is quite poor so going off-script is a no-no. She guides me through the steps needed to download some kind of remote-assistance client: Windows+R, type in iexplore remote.join360.net, jump through a few more hoops and run whatever executable is offered to you. From what I gather, this is actually a legitimate tech-support program, it being digitally signed and all.
The fun starts now. Patricia fires off cmd.exe after failing to recognize OllyDbg and IDA's icons on the desktop. In what I can only assume is a ploy to establish her technical expertise, she runs dir /s and tells me that the dates match my logins on this system and the files are all the documents I accessed. I feign amazement. Meanwhile, I stealthily send a CTRL+C into the terminal so we can go on with our lives. Patricia then types "1452 virus found", then "ip hacked", and asks me which antivirus software I'm using. None, I reply: they're too expensive and @taviso keeps breaking them anyway. The reference is lost on her but she chastises me nonetheless. Then something weird happens. She tells me that I'm at the end of my 15 minutes of free support and that she's calling me back so I don't have to pay. A few minutes later, I do indeed receive a call from a phone number in Pennsylvania (+1-267-460-7257). She goes back to berating me about my apparent disregard for basic computer hygiene. In the end, she reaches the following conclusion: my computer has been infected, and now it needs to be cleaned up. I'm encouraged to buy either ANTI SPY or ANTI TROJAN, for the measly sum of $189.90. Before I have the opportunity to get my credit card, she goes back to the terminal, runs netstat and tells me that there's someone connected to my machine at this very moment.
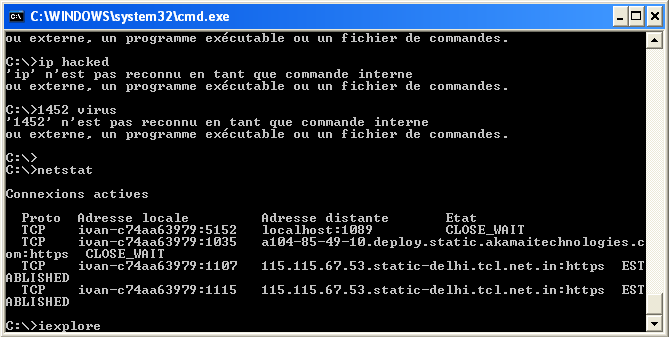
"Look! In the terminal! 1452 viruses found! Command not found also indicates that your machine is infected!"
By the way, I believe 115.115.67.53 to be their real IP address.
— Isn't that you? I ask. This says it's someone from Delhi.
An awkward pause follows. She tells me that she's actually the "localhost" line, because localhost means secure connexion. I fight back:
— Are you sure? I thought localhost meant the local machine.
She mumbles a little then proceeds to read me that whole section of her script again, asserting once again that this other IP belongs to a some who lives in Delhi like her but is a totally different person - a malicious hacker. I am not kidding you. We go back to the software she's trying to push.
— All right, I'll buy it, I say. Where can I purchase it in Paris?
Now she sounds quite annoyed.
— I don't know if you can find it in Paris, she replies with her choppy French accent. This is an exclusive software distributed only through Microsoft's premium partners and Microsoft's secure channels.
— Oh, so I just have to get it from microsoft.com then?
— ...Yes.
— Okay then.
— Okay.
— ...
— Did you have any other questions ? No ? Bye then.
Second call:
I assume that this is not how you scam people. She must have been a scammer trainee or something. At this point I realize that some of the screenshots I had taken were no good, so I wait half an hour or so and I call again. I was expecting to talk to the same person and tell her that I couldn't find anything on Microsoft's website, but it's someone new (Dileep) and I have to sit through the whole procedure once more. Dileep seems much more familiar with his script, and he adds some nice details such as showing me that my machine has a lot of stopped services which is "totally not normal". He goes on to tell me that my machine is infected as well, that he just cleaned it for free but he recommends that I purchase a Tech Protection subscription so I don't get viruses ever again. This package costs €299.99 which is way more expensive than Patricia's, but I assume that's because he sounds more experienced. I agree to purchase his package and find test credit card numbers as fast as I can. For obvious reasons, the payment processor rejects the transaction and we try again four or five times. In the end, I suggest using my second credit card and give him another random yet valid (as far as the Luhn algorithm is concerned) number. Dileep makes me repeat both payment details at least ten times and I play dumb. He calls his superior in the hopes of figuring out why the payment isn't going through. In the meantime, I hear other operators in the background repeating credit card numbers and CVVs aloud. I'm assuming they're not PCI-DSS compliant. That's when I'm hit by a stroke of genius. I open my "junk" e-mail folder where I find many samples of the latest Locky campaign - those .zip files containing a JS script which downloads ransomware. I grab one at random, drag it into the VM. The remote-assistance client I installed has a feature allowing me to send files to the operator. I upload him the archive and say:
— I took a photo of my credit card, why don't you input the numbers yourself? Maybe that'll work.
At first, Dileep ignores me. He makes me type in my information a few more times (he's persistent, I'll give him that), until I put my foot down:
— Look, Dileep, I'm old and my sight is not so good. It's starting to hurt, having to squint to read those tiny numbers. Also, we've established I'm no good with computers, how about you give me a hand here?
He says nothing for a short while, and then:
— I tried opening your photo, nothing happens.
I do my best not to burst out laughing.
— Are you sure? Sometimes my pictures have a problem opening on MacOS, are you on Windows?
— Yes, he replies. Your pictures are corrupted because your computer is infected. This is why we need to take care of this.
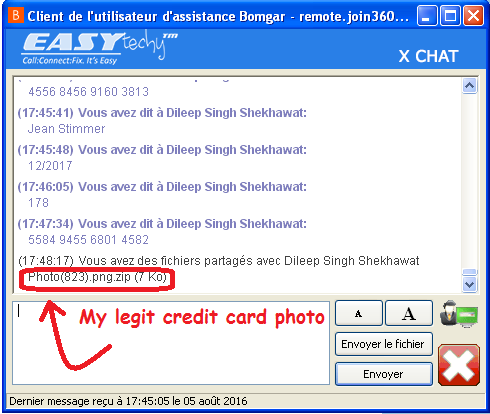
And while a background process quietly encrypts his files, we try paying a couple more times with those random CC numbers and he finally gives up, suggesting that I contact my bank and promising to call me back next Monday.
In conclusion, whenever one stumbles on an obvious scam, the civic thing to do is to act like you buy it. Rationale: scammers don't have the time to separate legitimate mugus from the ones who just pretend. Their business model relies on the fact that only gullible people will reply. Now were they spammed back, their workload would increase so much that scamming wouldn't be a profitable activity anymore. So if you're a French speaker, you should definitely take 15 minutes of your time, call them at +339 75 18 77 63 and try to social engineer them into doing something funny.