Whenever I post research on X/Twitter, and also at other random times, I get DMs from people who are interested in starting a career in the field. It’s not like I’m Internet’s guidance counselor or anything, but it’s gotten to a point where writing down a complete answer once and for all will save me a lot of time. Hence, without further ado, here are my unfiltered thoughts on starting a career in infosec.
Do you really want to?
The first question I would recommend considering is, how sure are you that this is a field you would like? Just like TV shows and movies produce a distorted perception of law enforcement work, the glamorous research published in infosec communities and conferences is not necessarily representative of the realities of the job.
I’m asking, because getting started in infosec is hard. To secure systems, you need to develop a deep understanding of them. To notice other people’s mistakes, you must be able to do things right in the first place. I don’t want to sound elitist and say infosec practitioners are better than other people (they really aren’t). The fact is, however, that they need more knowledge to accomplish their tasks. It is quite rare for people to accumulate the required knowledge unless they are passionate about the subject, so I would argue that being passionate is a core prerequisite.
That being said, did you know that there’s a huge turnout/burnout ratio in the industry? This is what happens when people get to do what they love while at the same time being set up to fail. I’m not pointing fingers at any specific employer or organization here. The fact is that cybersecurity has been a loosing battle for the past 25 years and that as of today, we’re no closer to a secure ecosystem than we were back then – it could be argued that we lost ground. It doesn’t mean it isn’t a battle worth fighting, but it takes a heavy toll on morale. As a cybersecurity practitioner, expect to report things that never get patched, face uncooperative users, and be denied both the financial means and authority that would be essential to your success.
I don’t want to paint too bleak a picture. I love cybersecurity and I’ve been having a blast since day one of my career, admittedly because I was lucky enough to be spared most of the unpleasantness mentioned above. But if getting into this field demands that you be passionate, surviving it relies on the rare ability to not care about failure. Passion plus disregard. It’s a weird and counterintuitive combination. That’s why cybersecurity is not for everyone – and if it’s not for you, it doesn’t make you any less of a good person. Or of a bad person. I don’t know you, you just cold-DM’d me after all.
There will be many times where you won’t succeed (and it will be through no fault of your own). If you can’t shrug it off, your mental health will take sustained hits.
Infosec is a huge field
Assuming you haven’t reconsidered already, you need to flesh out your career path in more detail. Anyone involved in medicine will tell you that the lives of surgeons and psychiatrists have little to do with each other. Cybersecurity is the same.
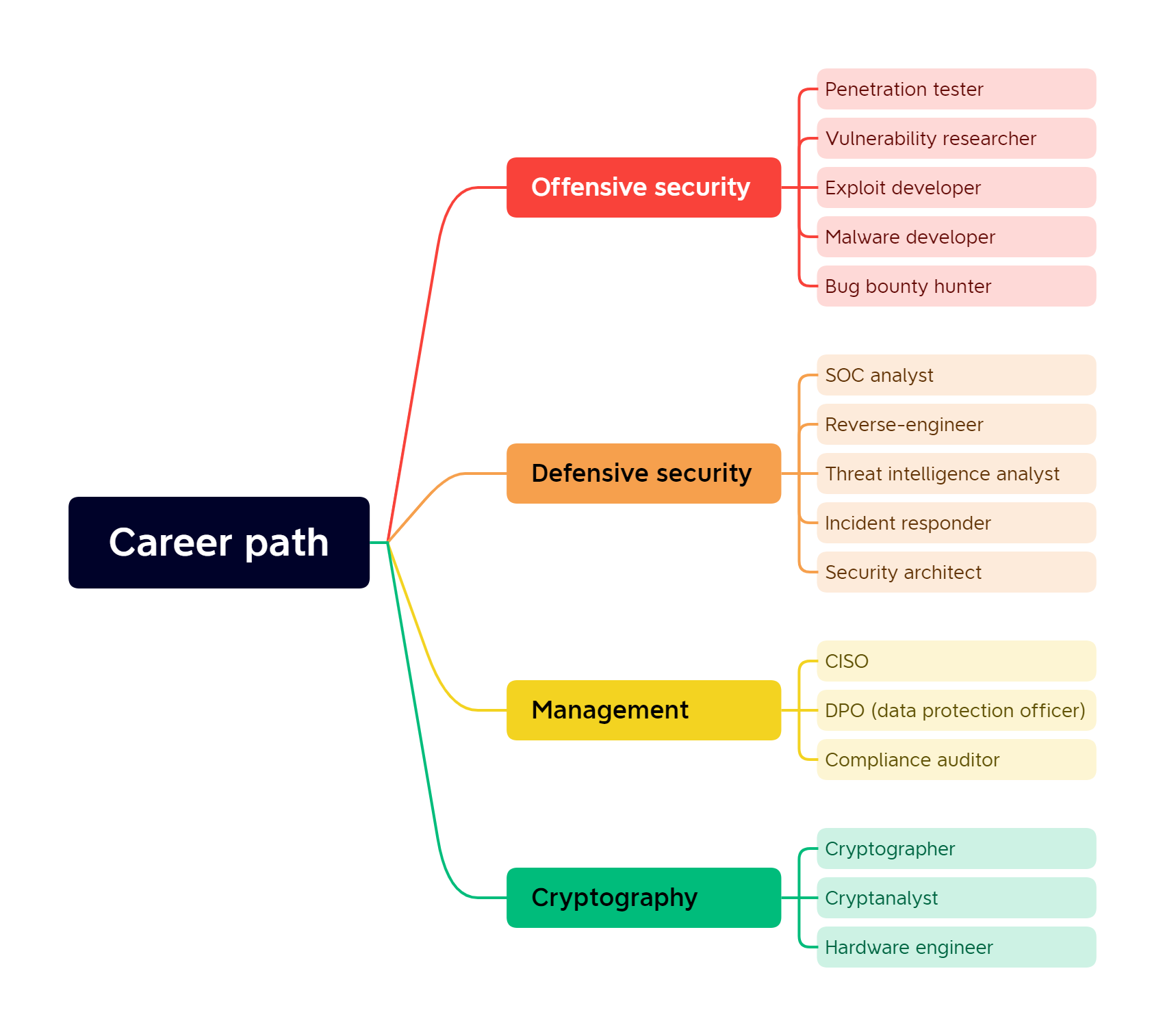
This is just from the top of my head, and there are likely many branches missing, but it serves to illustrate the variety of options you have. I personally specialize in reverse-engineering and threat intelligence, so there isn’t much I can say about the other positions. I would however feel remiss as an educator if I didn’t mention a few things:
- Offensive research is very appealing to people who are looking into entering the field. I suggest you are very careful which company you join, as a number of subfields (vulnerability research, malware development) are intrinsically tied to the surveillance industry. In their latest CCC presentation, Amnesty International demonstrated how such tools are leveraged against political dissidents, journalists and ethnic minorities. Their advice? Just don’t do it. No power trip is worth your soul.
- I have a personal disdain for bug bounty platforms. If you choose to go this route, remember that companies are the ones paying them – that makes you the product. In case of disagreement, they will almost always rule against you, and if you ruffle any feathers you’ll get banned. Bug bounty platforms are intricate systems for silencing researchers that also distribute occasional payouts as a side-effect of their operations. The less power they have over you, the better.
- If you’re considering malware analysis, make sure you actually enjoy reading assembly code. If you don’t, you’ll be miserable. 90% of university students I taught hated ASM, so don’t feel bad if you do. It’s not for everyone, find solace in the fact that you didn’t get the special kind of trauma that would have caused you to like it.
How to get started in cybersecurity in practice?
A lot of the people who DM me seem to be under the impression that I will take them under my wing, possibly as interns, and teach them the ropes. It’s not that I don’t want to (well, kind of), it’s that I don’t have the time. I can’t think of anyone in this industry who does. If you’re serious about getting into the field, you’ll have to figure it out mostly on your own.
It’s sort of unfair: the job market is structured in such a way that people with prior experience have a much higher chance of being recruited – a classic case of the snake biting its tail. Fortunately, there are a lot of resources out there that can help you bootstrap your technical skills. The first thing you need to do is learn a programming language (ideally two: C or C++ and a scripting language like Python). I can’t think of a non-management position in infosec where you won’t have to either write a quick program, or read someone else’s code… so you better bite that bullet as early as you can. C and C++ may not be the most popular languages today, but they’re still extremely educative due to how close to the CPU-level they operate. Once you’re comfortable with those, you will be able to move on to other languages with relative ease.
Next, you’ll need specialized education, depending on the field that tickles your fancy. Personally, I was able to get my first infosec position thanks to the OSCP certification. I see that it’s now twice as expensive as it used to be, but if you can afford it, I still recommend it wholeheartedly. Otherwise, there are probably cheaper courses out there, and a plethora of free challenges you can attempt to try your hand (and if you like it, you may consider joining a CTF team). These exercises tend to have their own internal logic that detracts them from real-life cases, but they’ll teach you actionable skills nonetheless. Alternately, there are hundreds of thousands of open-source programs on GitHub, all littered with bugs waiting to be found. Just do it!
For malware analysis, I developed a couple of online courses with my previous employer, I daresay they’re pretty good. I’ve also heard a lot of excellent feedback on this very cheap (1$) book. Many crackme programs can be found online, and to learn assembly in a fun way you can also check out Zachtronics’ great puzzle games on Steam. Then you can download actual malware samples at no cost on VirusShare (registration required) or MalwareBazaar: pick any one and analyze it, all that matters is that you’re able to work through an analysis on your own.
Finally, have a look at anything published by No Starch Press on your favorite subject, as they provide really good beginner-level material.
Extra miles
An excellent way to demonstrate your passion for the field is to publish what you do. If you write a cool program that solves an issue you had, put it on GitHub. If you reversed-engineered a program or found a minor bug in some random application you found online, write a blog post about it. This will put you miles ahead of other applicants who can only talk about how much they like the idea of cybersecurity.
Do not count on degrees and certifications too much. When I was a student, cybersecurity degrees weren’t really a thing. Now it’s gotten a little better, but I’m still not convinced there’s enough time in a school degree to teach everything needed to get into cybersecurity (I’m saying this as someone who was involved in such curricula). If you’ve been taught the basics, good for you, but you’ll likely need to do a bit more on your own. If you weren’t, don’t feel too bad because you’re not that much at a disadvantage.
All in all, the most important aspect is that you do things and show a capacity for autonomy by learning on your own. If you can, find people who are also starting out (at school, on forums, Discord, etc.) and hone your skills together – but don’t jeopardize your future by doing anything illegal.
As a recruiter, I would not expect a lot of technical expertise from a junior, but I would expect them to show me something beyond mandatory homework – otherwise I will assume that the applicant lacks the base interest required to thrive in the field, or that I’ll be forced to do more mentoring than I wish to.
Conclusion
I think that covers everything on getting started in infosec. I hope this post didn’t discourage anyone; at the same time, I think it’s important to ensure people don’t head straight into depression by getting in the field unaware. Note that everything laid out above is only my personal opinion and that many respected cybersecurity practitioners may have different views on the matter. I recall a Twitter debate, a few years ago, where people were protesting the notion that working in infosec required a special kind of passion. They denounced that position as elitist and argued that it promoted unhealthy work habits. Maybe they were right. Yet I remain convinced that cybersecurity, as a subject matter, requires too much personal involvement and stubbornness to be treated as any other random job.
It is unlikely that I will settle this debate here, however I think everyone would agree with the notion that if there’s something you’re really passionate about, it’s likely what you should be pursuing (whether it’s cybersecurity or not). And if it is, while it will require some effort on your part, odds are you will make it because the industry is actively looking for more people. Good luck!

