A lot has been going on at the intersection of AI and the art field recently. There's a lot to say about how AI will change our lives, and I feel that the current debates are missing the point.
I've laid down my thoughts on the subject here:
https://www.kaspersky.com/blog/chat-gpt-changes-all/47405/
TL;DR:
This essay was published on VentureBeat on December 19, 2021.
Smart people in my industry have noted the growing role of cyberspace in inter-state conflicts and called for the development of cooperative, global regulation and governance. There are a few ethical dilemmas that this raises, including one that not much has been written about: the morality of cyberattacks.
In 2022, some time before FTX's demise, I wrote a long three-part series on cryptocurrencies and NFTs which was published on Kaspersky's blog. It was translated in several languages, and I thought it would make sense to put all the links on my blog. It ended up being my biggest writing project for the year and I'm very proud of the way it turned out. I hope you'll find it an interesting read!
Tags
Hey everyone. I haven’t posted here in a while. The world made no sense the last time I did, and it makes even less sense now. That translates (among other things) to people being crazier on the internet, constantly challenging my personal illusions about what I imagined to be rock bottom. Maybe in five years, I will come back to this post, read it again, and go “oh, man, those were the chill days, I miss those”.
A few days ago, Kaspersky published a blog post regarding a likely false flag in the wiper component of OlympicDestroyer. The attempt is based on an undocumented, lesser-known PE header called the RICH header. I don’t want to go into too much details regarding its layout, as many other sources have done a great job documenting it.
These are troubled times indeed. If you’ve been using the Internet for a while, you must have noticed that the general climate has been steadily declining. In fact, it feels like we have grown quite used to our weekly offense-fest. It is speculated that social media platforms are engineered in a way that encourages them: nothing generates more “engagements” than an inflammatory post that the audience will retweet in feverish, self-righteous anger. The mainstream media certainly doesn’t seem to mind, as this provides a constant stream of highly clickable opinion pieces.
Tags
For some reason, articles about process injection techniques seem to be popular these days, and I thought it was the perfect opportunity to write something I have had in mind for a long time. As some of you may know, I maintain Manalyze, a static analyzer for PE executables. One key part of this program is obviously its parser, as writing PE parsers is notoriously hard. For this reason, I took great pains to make sure this part of Manalyze could be reused in other projects.
Tags
Today's article is going to be a short one. Many of you may have read @ropnop's great post on upgrading plain shells to interactive TTYs. While the commands given in the article can solve usability problems, they provide no help on the transport level where several things can go wrong:
Tags
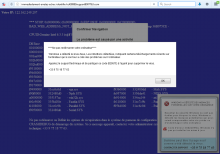
A few days ago, I received a panicked call from my parents who had somehow managed to land on a (now defunct) web page (snapshot here) claiming they had been infected by Zeus. This horrible HTML aggregate had it all: audio message with autoplay, endless JavaScript alerts, a blue background with cryptic file names throwing us back to Windows' BSoD days, and yet somehow it displayed a random IP address instead of the visitor's one.